SPONSORED BY: Integration Objects
In the age of Industry 4.0, the integration of IT (Information Technology) and OT (Operational Technology) systems, the use of IoT (Internet of Things) devices, along with technology adoption evolution on the OT side, has led to an unprecedented peak of cyber security threats targeting industrial systems. The business impact is considerable including operations interruption, system shutdowns, and confidential data breach. Consequently, end users took several measures to secure their OT networks.
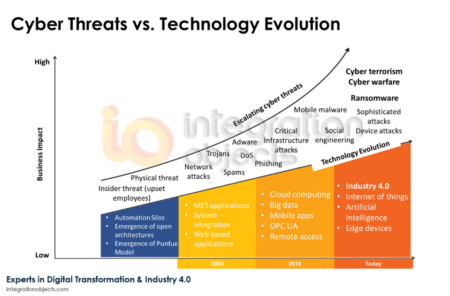
However, the advancements of cyber security on OT come with unique system integration and network challenges as systems need to communicate across firewalls, NAT devices, and other network barriers. The need for secure and seamless data flows between IT and OT has never been more pressing as it remains crucial to operations efficiency and decision making.
Let’s first identify the challenges introduced with modern industrial networks that implement cyber security measures:
Challenges of Modern Industrial Networks
- Firewalls and NAT Devices: Many industrial systems are located behind firewalls or NAT devices and DMZ that restrict incoming communications. This makes it difficult for systems on the “outside” such as an IT system or application to connect to OT servers or devices that are protected by these network barriers.
- Security Concerns: Given the critical nature of industrial systems, maintaining the integrity and confidentiality of data while ensuring seamless communication is crucial.
- Integration Complexities: Legacy systems, new IoT devices, and cloud-based platforms often use different protocols and security models. Integrating them into a unified system can be a daunting task, especially when network constraints or security policies restrict direct connections.
Adopting the OPC UA communication protocol to expose OT data has resolved many of the cyber security challenges for industrial systems. In particular, OT data communication across firewalls and DMZs are enhanced using OPC UA Reverse Connect. This OPC UA functionality allows users to establish secure OPC UA connections across firewalls, without the need to open in-bound firewall ports.
Adopting OPC UA Reverse Connect on Existing OT Infrastructure with SIOTH® Platform
One solution to these challenges is the concept of OPC UA Reverse Connect. Unlike traditional methods where a client initiates a connection to a server, OPC UA Reverse Connect allows the server to initiate a connection to the client, while complying with cyber security rules configured in firewalls and NAT devices.
Many OPC UA implementations lack built-in support for Reverse Connect, creating challenges in environments with strict network constraints. SIOTH® (Smart IoT Highway) bridges this gap, enabling seamless and secure communication between OPC UA clients and servers. SIOTH® incorporates the Reverse Connection Capability to enable secure and reliable communication between IT and OT systems, even when behind firewalls or NAT devices.
With SIOTH®’s Reverse Connection, the connection process is simple yet effective and is often used when an OPC UA client needs to establish connections with one or more OPC UA servers that are located behind a firewall or NAT device. To activate this capability in SIOTH®, SIOTH® provides 2 main components:
- Bridge Client to be deployed on the OPC UA client-side network, typically the IT or DMZ network
- Bridge Server to be deployed on the OPC UA server-side network, typically the OT network
To establish the communication between the OPC UA Client and the OPC UA Server behind the firewall using SIOTH® Reverse Connection Capability, the following high-level sequence is performed:
- The OPC UA Client connects to the Bridge Client via its endpoint and request connection to the target OPC UA Server. This request will be tunneled to the Bridge Server via the control channel.
- The Bridge Server will connect to the target OPC UA Server after security constraints verification.
- The Bridge Server will open a new connection with the Bridge Client dedicated to tunnel this OPC UA communication. This new connection will be a dedicated channel to respond to the OPC UA Client requests and securely forward them to the OPC UA Server such as read and monitor data in real-time.
Building on its ability to overcome network barriers, the Reverse Connection Capability in SIOTH® is further enhanced with advanced features from the SIOTH® platform such as:
- Unified communications via OPC UA Universal Server, allowing users to migrate their legacy systems and other OT data sources to support OPC UA.
- Data confidentiality and integrity by using data encryption, whitelisting, user authentication techniques.
- Robustness against network glitches via automatic reconnection, store and forward capability and configurable communication timeouts.
The versality of SIOTH®’s Reverse Connection Capability extends to a range of industrial scenarios, addressing critical networking needs with ease and efficiency. Key applications include integration between IT/DMZ systems and OT data sources. SIOTH® allows for integration between IT/DMZ systems and OT systems without requiring changes to existing firewall rules, ensuring secure and reliable data exchange while providing protocol conversion and data transformation capabilities.
About Integration Objects
Integration Objects is a world-leading industry 4.0 solutions provider for digital transformation, advanced solutions in machine learning and predictive analytics, integrated command & control centers, Cloud services, industrial internet of things (IIoT), cyber security, OPC and Big Data Analytics, for process, power and utilities industries, defense, and governmental institutions.