SPONSORED BY: Software Toolbox

Then need to secure OT data integration with IT, business and the cloud is imperative beyond just critical infrastructure industries. Every industrial operation’s success depends on effective, pragmatic security measures and use of current technologies.
OPC UA interoperability standards natively include functionality to sign & encrypt data in transit, authenticate access, identify applications that we’ve talked about in a prior article in OPC Connect. As strong as those OPC UA functionalities are, they only apply to data that can flow through OPC secured connections and there are other considerations to securing your OT data.
In this article we explore considerations and solutions for the security of the applications used to integrate hardware and systems with OPC UA including those that convert OPC Classic based systems to OPC UA.
Application Security Helps Get the Most from OPC UA Security
When building your secure OT integration architecture, you need to also consider how applications secure access to their configuration and the data sets within them. Without doing that and only focusing on data in transit on the network, you don’t have a complete solution. Although outside of the OPC UA interoperability standards scope, but just as important to maximize the benefits of using OPC UA.
Common methods of securing applications include but in today’s world are not enough:
- Requiring authentication to access configuration applications and stored configurations
- Minimum password length and complexity requirements
- Providing means to limit access to parts of the configuration and types of changes by user
In our nearly 30 years of experience empowering and supporting users & integrators using real-time middleware applications to integrate systems of varied age with modern technologies, we believe that even more application security is required.
Securing Gateways and connections to OPC Classic Systems
When using real-time middleware gateways to bring together OT, IT and cloud systems, the range of security options available is varied, and sometimes the other systems inherently limit how far the gateway developer can go, but it’s important to do as much as is practical. The gateway software is just one piece of the puzzle, and it’s important that industry best practices such as the US NIST Cybersecurity Framework are followed to complement what the application developer can do.
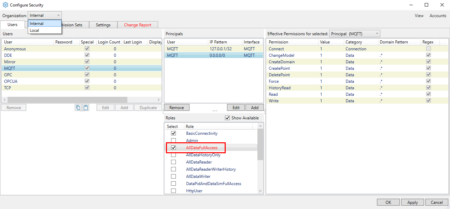
As an example of this, in the latest version 11 of the Cogent DataHub, a real-time OT/IT/Cloud integration middleware solution, the developers have taken the application security capabilities to a new level in multiple ways you can learn about in detail in our technical blog post on DataHub V11 security.
- Role based permission assignment
- Multi-factor authentication including time-based one-time passwords for access to configuration
- Ability to assign individual user permissions by connection source (IP, etc), and connection protocol such as OPC UA through user defined security principals to define login contexts
- Robust, detailed granular permission sets
- Integration with Windows Active Directory via LDAP
- Warnings about insecure configurations
- Change report showing impact of a change before committing the change to production
- Native integration with the OPC UA client and server interfaces in the software to supplement the already robust security OPC UA provides.
When integrating existing systems, it’s not always possible to use OPC UA right away. Rip-and-replace is not practical in many industrial systems. You may have software where suppliers have not updated their products yet to offer a clear path to OPC UA or they have only done it for their OPC DA interfaces but not other OPC classic systems.
And then there are non-OPC UA systems such as connections to databases, historian, alarms & events servers, legacy device protocols and more. Although there are practical limitations based on those other systems that may limit security options, you want the application you bring them into to be secure. That’s where the Cogent DataHub comes in and the new V11 application security is even more important.
OPC Classic and Other Systems to OPC UA Conversion
A benefit of working with Software Toolbox is our OPC experience that dates to the start of the standards. We’ve seen a lot of different user architectures and apply that to help you with your initiatives to use data to improve your business decisions, no matter what applications you use.
When it comes to modernizing your OPC Classic system architectures on a schedule that meets your budget and needs, Cogent DataHub excels at converting OPC standards for multiple reasons:
- Real-time performance of up to 100k data changes/second with minimal latency
- Scalable to over 2 million tags in single 64-bit application instance
- Extensive configuration options
- Robust security, especially with V11’s enhancements
The number of possible reference architectures and DataHub solutions are extensive, but here are some examples of things we’ve helped users accomplish.
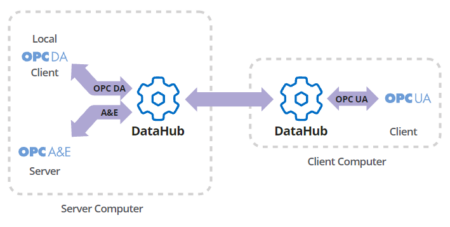
OPC DA to OPC UA to OPC DA
The most common conversions users implement using Cogent DataHub’s OPC DA client & server support are:
- From an OPC DA Server that doesn’t support OPC UA, to an OPC UA server to enable OPC UA clients to connect remotely and avoid using DCOM
- From an OPC UA server, tunneling to a DataHub acting as a UA client and then serving data via OPC DA, to an OPC DA client that does not yet support OPC UA

OPC HDA and Non-OPC Historians to OPC UA Historical Data
New to CogentDataHub V11 is the ability to connect to OPC Classic HDA servers and deliver the data to OPC UA Historical Data clients.
Also new to V11, you can pull data from a variety of supported external historians, including InfluxDB, and serve it to OPC UA Historical Data clients in just a few steps.
OPC Alarms & Events (A&E) to OPC UA Alarms & Conditions
In addition to being able to generate alarms, serve them to clients, and generate notifications from any data source that it can connect to, Cogent DataHub’s OPC UA Alarm & Conditions support can also
- Convert OPC A&E to OPC UA Alarms & Conditions
- Convert OPC A&E and OPC UA Alarms & Conditions to tag sets representing the parts of an alarm structure for use with clients that only support OPC DA or OPC UA data access.
- Securely tunnel data between OPC A&E servers and clients through firewalls, proxies, and DMZs
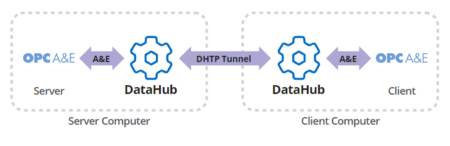
Secure Data Tunneling & Conversion to OPC UA
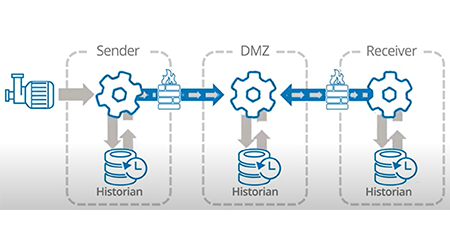
Cogent DataHub is best known for its secure, lightweight DMZ & proxy friendly data tunneling for OT to IT & business data sharing. OPC UA can be used for data tunneling but as we’ve shown, when integrating systems that are not natively OPC UA, you need security until you get to OPC UA. DataHub complements and supports OPC UA in these applications.
Rather than use an insecure legacy protocol, there are many options available to get your data to an OPC UA enabled system. Examples include:
- Put a DataHub instance on the non-UA system and then securely tunnel it over to a DataHub that is aggregating data into a common namespace, for delivery to OPC UA enabled systems as a UA client or server
- Use the DataHub instance installed on the legacy system to convert to OPC UA either as a client or server, and benefit from DataHub V11’s application security along with OPC UA secure data transport to UA clients and servers.
Below are a couple of example architectures, from simple read/write tunneling to advanced tunneling through a DMZ and proxies with all in-bound firewall ports closed on the OT and business layers.
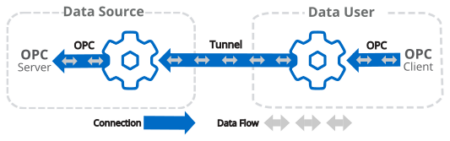
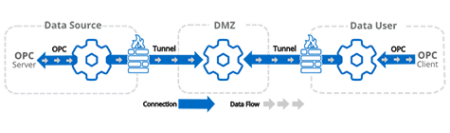
With DataHub V11, a new secure data diode tunneling mode was added to the tunneling functionality. When enabled this mode will discard all incoming data without any processing, further enhancing the ability to have data only originate from the DataHub. Hardware data diodes that use TCP emulation are also supported for even more data integrity assurance.
Conclusion
The promise of OPC continues by empowering best-of-breed solutions that bring together applications at all stages of their lifecycle. OPC UA provides native security in the standards. Off-the-shelf software from Software Toolbox supported by our responsive, available experts empowers your success no matter where you are in your journey. We invite you to learn more about all our solutions!
About Cogent DataHub
Cogent DataHub is a modular, configurable middleware software application designed for real-time integration of data in industrial applications at any level. Connectors for OPC as discussed here are complemented with native bi-directional connectors to Historians such as AVEVA PI System, AVEVA Historian, InfluxDB, and many others. Databases of all types are supported for read & write access. Store & Forward support ensures data arrives at its destination without loss. Datahub can be extended further with email notifications, Excel & Modbus TCP connections and more.
Multiple ways to consume, organize, and deliver data securely to cloud applications for AI and Machine Learning empowers an endless array of solutions without writing custom software applications.
Request your Cogent DataHub Free Trial
About Software Toolbox
Software Toolbox, founded in 1996 and a Charter Member of the OPC Foundation, was the world’s first industrial automation software company focused on software that leverages open standards for OT, IT, business and now cloud systems. Through our early leveraging the internet for global support reach we’ve built an installed base on every continent (yes even the South Pole Station!), they are known for their technical expertise across their variety of solutions that empowers success and reduces the risk of multi-vendor applications. Our raving fan users that trust our brand are a clear testament to the value we provide through the Software Toolbox way.