The need to share process data between production sites, refinery, petrochemical, gas and utility plants has been increasing for the past decade. These plants and production sites are typically located in the same area and have the need to exchange feed stocks, naphtha, ethane and utilities streams such as hydrogen, electricity, water, steam, and fuel gas, which created the requirement to exchange data between their metering and control systems.
With the tight network security policies of the different companies in the chemical, oil & gas and utility industries, it has become significantly challenging to integrate with third party systems. Integration Objects has designed an OPC based solution to enable such integration while complying with the ISA 99 network security standards and the different stakeholders’ policies. Such systems have already been deployed successfully to integrate refinery, utility, oil & gas stabilization, and LNG plants.
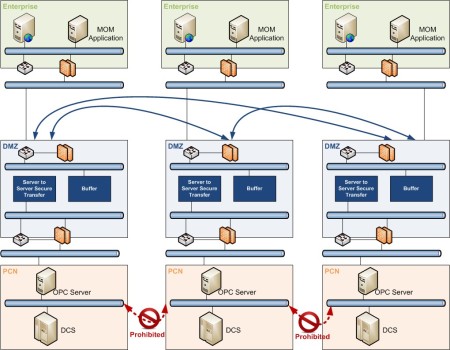 Companies with rigorous cyber security policies protect their process control assets by implementing a demilitarized zone (DMZ) physically separating and eliminating direct communication between the enterprise and the control networks. The challenge is how to continue exchanging critical data for accounting, safety and controls purposes with third party systems without introducing security risks, and at a minimum cost.
Companies with rigorous cyber security policies protect their process control assets by implementing a demilitarized zone (DMZ) physically separating and eliminating direct communication between the enterprise and the control networks. The challenge is how to continue exchanging critical data for accounting, safety and controls purposes with third party systems without introducing security risks, and at a minimum cost.
Overview
Integration Objects’ OPC based secure solution for DMZ allows users to exchange critical data with third parties in realtime while:
- Respecting security policies of all stakeholders and ensuring the confidentiality of their data
- Benefiting from an OPC UA interface allowing applications at the enterprise level to also securely send data back to the control system through the DMZ
- Avoiding significant capital investment as the solution takes advantage of the existing classic OPC based infrastructure.
Data Flow
The secure DMZ hosts a buffer that does not have any read or write capabilities, and includes only the tags that are needed for the specific data exchange. The server-to-server secure transfer, located in each side, will collect the data, on as needed basis and from the DMZ buffer, and will then transfer it to the OPC Server located in the process control network (PCN) and vice versa.
Security
All transferred data are encrypted to ensure data integrity and confidentiality. In addition, the data access requires user authentication from the buffer server level down to the tag level.
- User authentication is based on Active Directory in order to confirm the identity of the user trying to connect and access the data. This mechanism prevents unauthorized access that can be issued either internally or from an outside network.
- Granular access rights are configured using user profiles and specifying the set of permissions that defines which tags assigned users are allowed to browse, read or write, or read/write.
The firewalls are configured such that only one TCP port is authorized. This port can change any time at the discretion of the network security team of each company. All of these security features are easily configurable using a user friendly graphical interface and do not require a public certificate provider or access to the Internet.
Advantages
The solution has the following main advantages:
- None of the DMZ is bypassed. All communications with the PCN are initiated from the DMZ and are not based on classic OPC/DCOM.
- The communications between the PCN and the DMZ are reestablished automatically after recovering from network glitches.
- Only a single TCP port is needed to be open in the firewalls. This port is configurable and is not a public or known port. Moreover, each party can use a different port for the communications to their PCN and does not need to disclose this information to the third party.
- Data is encrypted and therefore, it is invisible to hackers, as it does not allow any spoofing or sniffing.
- Using OPC UA, applications at the enterprise level such as production planning or asset optimization applications can also securely exchange data with the control system through the DMZ.
- The remote communications can be established from different domains, across VPN and through WANs. Users can also fine tune communication timeouts and data compression parameters for better performance of data transfers across their network.
Note: Given the critical nature of such application and the number of companies involved in implementing this solution and their security policies, we were not able to obtain a common authorization to expose the success story. The following is a quote of the project manager, one of the stakeholders:
“Our project of integrating our systems with third party networks was delayed by nine months because we could not find a solution that works and complies with our network policy and all the third party’s involved. We were pleasantly surprised to see Integration Objects providing not only a highly secure solution, but an OPC highly robust one”.