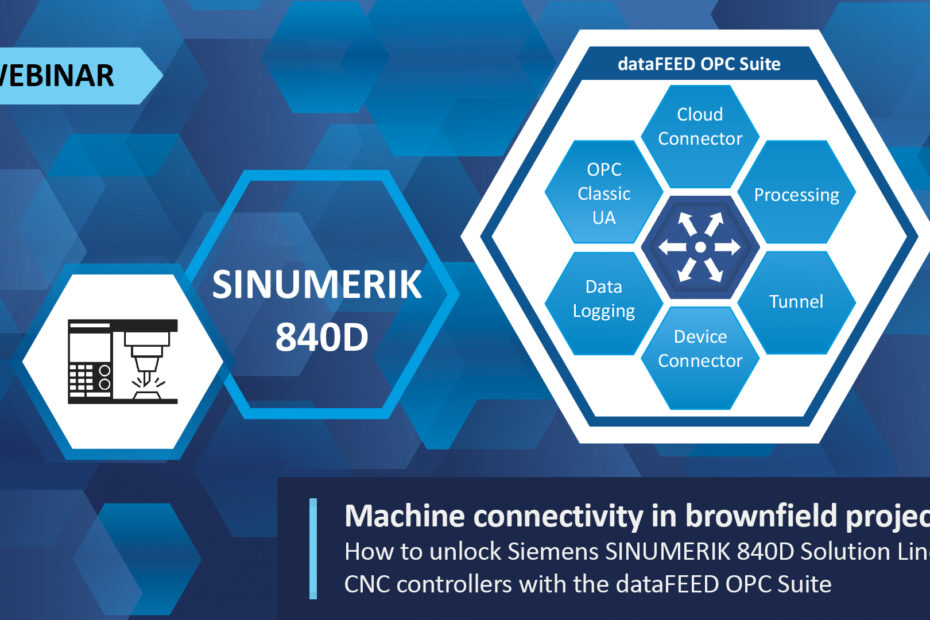
Machine connectivity in brownfield projects: How to unlock Siemens SINUMERIK 840D Solution Line CNC controllers with the dataFEED OPC Suite
SPONSORED BY: SOFTING Webinar alert, July 9, 2024: Machine connectivity in brownfield projects: How to unlock Siemens SINUMERIK 840D Solution Line CNC controllers with the… Read More »Machine connectivity in brownfield projects: How to unlock Siemens SINUMERIK 840D Solution Line CNC controllers with the dataFEED OPC Suite