SPONSORED BY: Utthunga
Securing plant floor data and managing IT/OT convergence risks
One of the most common use cases that Industrial Automation presents is the convergence of Operation Technology (OT) with Information Technology (IT). The term “convergence” for sure has raised a lot of eyebrows and continues to do so considering the risk of cybersecurity and the vulnerabilities in the network that is involved. But the other side of this argument presents significant business benefits when implemented correctly.
Originally, this convergence of OT to IT was primarily implemented for the purposes of:
- Business Process Reporting
- Billing
- Regulatory Data
The objective was to reduce human reliance and intervention in business process related reporting activities as highlighted above.
But, with the introduction of new technologies in the Industry 4.0 and IIoT landscape, this OT to IT convergence has led to use-cases like:
- Predictive maintenance
- Improvement in Efficiency
- Condition monitoring
- And other plant floor process specific applications
We are now starting to see large amounts of data being consumed and processed by manufacturing analytics platforms and this has resulted in use-cases like:
- Remote troubleshooting
- Enterprise cyber asset management
- And other security related management across both IT and OT functions
For OT data to be consumed seamlessly by the Enterprise applications in IT, there should be a sense of openness in order to facilitate co-existence and interoperability, which in turn provides a competitive landscape for the choice of best-in-class products. But, for this to happen, there is a significant stance on security that is required in the form of security policies, compliance with standards, business practices, etc.
Due to these security related challenges during the OT & IT convergence, many organizations and industry bodies recommend segmenting or buffering the OT and IT world by using an Industrial Demilitarized Zone (iDMZ).
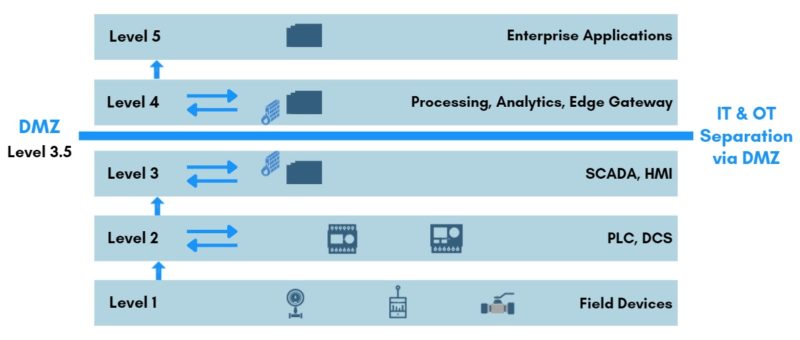
DMZ & Level 3.5
This Industrial Demilitarized Zones (iDMZ) exists as a separate network level between the OT world (Industrial) and the IT world (Enterprise). And this is commonly referred to as Level 3.5. Typically, to facilitate this demarcation between the two layers, there are different combinations of hardware and software solutions that are deployed. For example, firewalls, VPN servers, application mirrors, proxy servers, switches, routers, etc. These solutions ensure that a strict data security policy is enforced between a trusted and untrusted network.
OPC UA PubSub
Conventionally for data to be exchanged between different levels, a Client/Server model was used and still forms a large portion of the existing data exchange topologies in Industrial Automation applications. This is based on a simple concept that a passive Server component exposes data for other applications that act as Clients. Hence, the client applications can access data from the Server via standardized services.
However, this architecture has presented challenges such as:
- Not suitable for unreliable networks
- Inability to handle large number of connections resulting in resource overloads
Taking these problems in consideration, the OPC Foundation introduced OPC UA PubSub mode of communication. As the name suggests, the OPC UA PubSub model inherently includes a Publisher and Subscription component respectively. In this model, the messages from field devices are published to a Broker, and different Subscribers can listen to them and decide which portion of the data they want to consume.
Pub-Sub overcomes these issues of the conventional Client-Server architecture:
- Faster response time in communication.
- Ability to operate in unreliable networks, where the data is published and stored in the broker until the subscriber consumes the information when the connection is established.
- Highly scalable architecture can be deployed in large networks with hundreds and thousands of devices publishing and subscribing the data from the Broker.
These benefits have opened a whole new way of data communication between two automation products and OPC UA PubSub has already become the most sought-after standard to move plant data to cloud due to the in-built SHA 256 encryption algorithm for privacy & security.
An important use case of OPC UA PubSub is to use it as a DMZ Gateway between two separated networks, which in this case is OT and IT.
OPC UA PubSub as a DMZ Gateway
PubSub allows using OPC UA directly over the Internet or the cloud using middleware like MQTT (Message Queue Telemetry Transport) and AMQP (Advanced Message Queuing Protocol). Therefore, none of the applications communicate to each other directly. The middleware acts as a broker that directs messages.
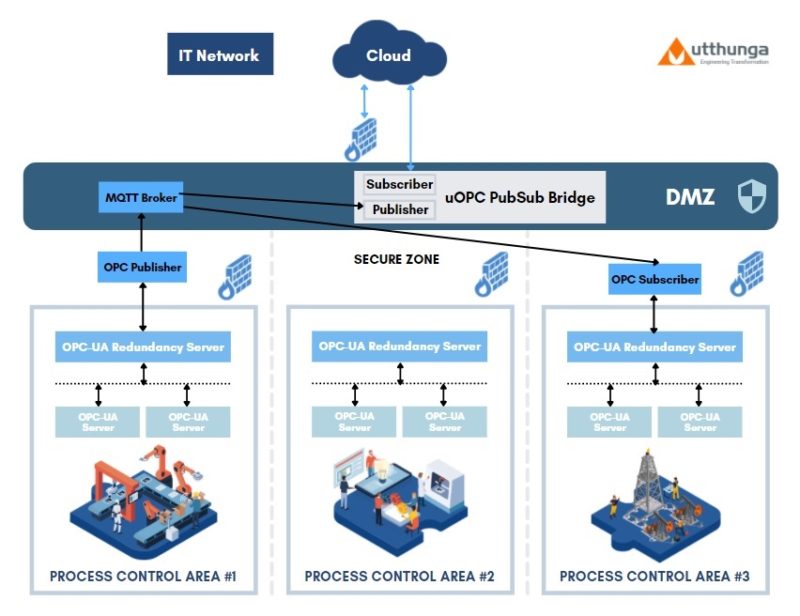
The architecture explained in the next section shows a representation of a typical setup where there are multiple Process Control Areas that have OPC model data flowing from field devices.
Utthunga’s uOPC PubSub Bridge plays the role of a DMZ gateway, where in, the OPC data from these Process Control Areas are published to a MQTT Broker. And the Enterprise applications in the IT layer subscribe to the uOPC PubSub Bridge to consume the data without having to multiple inbound ports in the IT side firewall and expose the network to cybersecurity attacks & vulnerabilities.
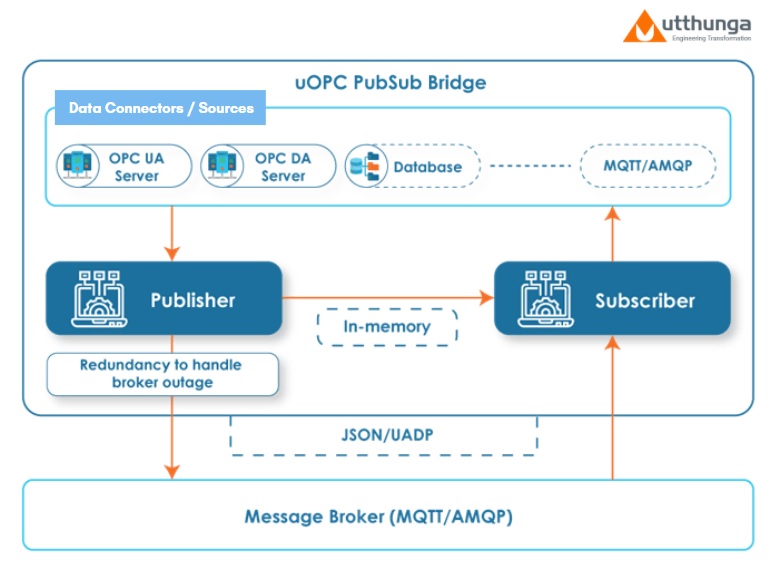
uOPC PubSub Bridge
Utthunga being an early adopter of OPC UA PubSub model and contributing to the PubSub working group, came out with the uOPC PubSub Bridge that is built to be compliant with the latest OPC UA specification.
This product addresses the above-mentioned challenges in a more secure and streamlined fashion. Here the OPC applications take the role of publishers and subscribers with messages being exchanged via a middleware. The Message Oriented Middleware supports connecting, sending, and receiving messages between distributed applications with the help of protocols.
The uOPC PubSub Bridge also offering seamless integration with other data connectors in the Industrial Automation framework using an API layer.
Over the years, this uOPC PubSub Bridge product has seen a wide range of use cases:
- Acting as DMZ Gateway across domains using OPC UA PubSub Mechanism
- Connecting Process data or Point Cloud data to Cloud platform
- Connecting OPC DA data to Cloud platform
- Enabling loss free transmission over noisy connectivity link
- Acting as a Protocol Bridge
Below architecture shows how the PubSub Bridge’s Publisher & Subscriber components are used to implement a DMZ Gateway scenario.
By providing access to near real-time data, large chunks of data and ensuring end-to-end security, the uOPC PubSub Bridge has proven to be a key enabler for digital transformation in different industrial applications.
About Utthunga
Utthunga is a Product Engineering and Industrial Solutions company. We engineer industrial-grade digital products and solutions for industrial OEMs, Industries, ISVs, and Service Providers. We provide software development, firmware & hardware development, IIoT applications, IT-OT integration, field device integration, industrial communications, security engineering and testing services to global industrial OEMs and manufacturers. Besides these horizontal technology offerings, our domain-based vertical expertise in Process, Factory, Power, Building and Mobility domains enable us to function as a very dependable partner for our customers across the globe.
Utthunga is a corporate member of the OPC Foundation and has been a staunch proponent for the OPC standard and we continue to support 50+ industrial automation OEMs and organizations in their OPC implementation journey. www.opcfoundation.org/members/view/2531
To learn more about Utthunga & uOPC PubSub Bridge, Visit: www.utthunga.com/products/opc/pub-sub-bridge